
Much before the onset of the global pandemic, managements faced challenges with the ever changing and dynamic digital environment.
Today, all information and communication are in the digital space. Be it, communicating with employees, suppliers, customers, tax authorities, etc or recording of production and accounting numbers, bank payments, etc. Despite the lurking danger to the sector and the constant digital war, cyber risk management and reporting have been grossly understated and managed. Hackers are waiting to unlock the security system put in place by governments, companies, homes and internet service providers.
Cybercrime is expected to cost the world about $6 trillion in 2021 alone. Cybercrime cost includes deletion, damage, unauthorised edits to data, loss of funds, impact on productivity, intellectual property theft, theft of personal communication, brand damages, lack of trust, financial data, embezzlement/frauds, disruption of normal business services, etc.
Cyber threats lie in wait everywhere both internal and external, it can be intentional or un-intentional.
Today, in this age of work from home, governments and management in all sectors have enhanced the understanding of the risks.
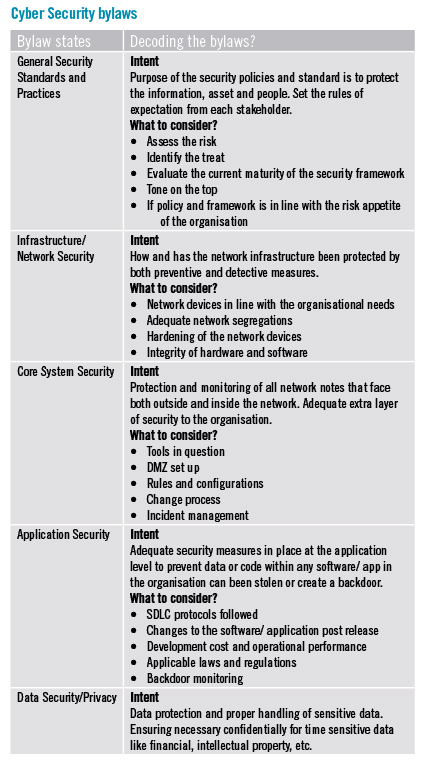
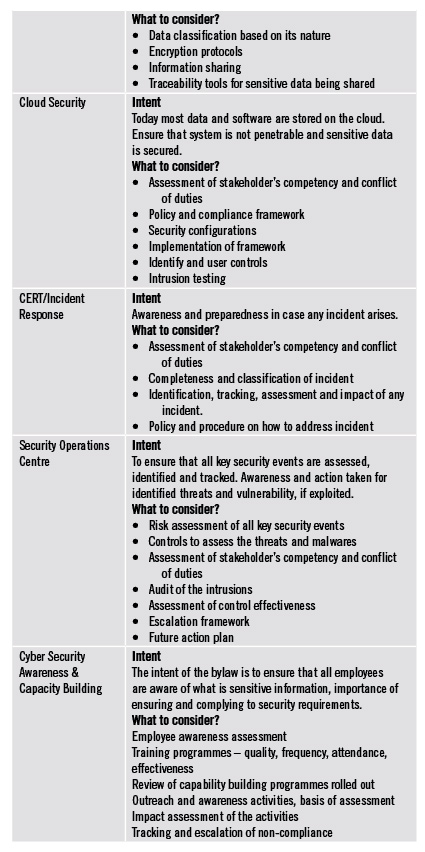 The bylaws have been defined by NTA benchmarks to both the service provider and the auditor. The checklist should not be considered verbatim for the purpose of audit compliance. The overall intent of the government body is to protect the user of service and provider of service from any malicious attacks and threats and build confidences in the technology and service.
Keeping the overall intent in mind, we should take this opportunity to assess the overall maturity of our cyber security framework and addressing any vulnerabilities and threats we find in the process. As we all would agree, change is the only constant thing in life, and so is the lurking threat of hackers with malicious intents.
READ ALSO:
The bylaws have been defined by NTA benchmarks to both the service provider and the auditor. The checklist should not be considered verbatim for the purpose of audit compliance. The overall intent of the government body is to protect the user of service and provider of service from any malicious attacks and threats and build confidences in the technology and service.
Keeping the overall intent in mind, we should take this opportunity to assess the overall maturity of our cyber security framework and addressing any vulnerabilities and threats we find in the process. As we all would agree, change is the only constant thing in life, and so is the lurking threat of hackers with malicious intents.
READ ALSO:
Need of the hour for telcos and ISPs
Fortunately, some leading government sectors in Nepal are pioneering the change, regulators are creating and asserting the need for privacy, stronger controls, protection of sensitive data. For example, Nepal Telecommunications Authority (NTA), that issued Cyber Security Bylaws 2077 under the Telecommunication Act 2053. The bylaws have been framed for implementation of cyber security standards, best practices so as to protect Information Communication Technology (ICT) against malicious attacks and threats; and build trust and confidence of users towards the ICT partner, technology and services in use. As per the bylaws, organisations need to ensure adequate security, policies, controls around various factors associated with cyber security like data, network, application, endpoint, mobile, end-point, identity and access, disaster recovery, etc. Speaking to stakeholders required to comply with the bylaws, we realised, there was a need for clarity on the level of compliance needed to the bylaws. There are a few critical and commonly benchmarked standards across the global like COSO, COBIT, IS 27001, NIST standards, etc. These standards set the ground and tone for any cyber security implementation, review and compliance. Based on our conversation with NTA, we realised, their objective from this information security audit is to arrive at a sense of comfort that the telcos and ISPs do not have any gross vulnerabilities that can be exploited and potential access to sensitive data. We dove deep into the bylaws to understand the intent and things that the companies should consider. This is not a 100% list, only an indication.
 The bylaws have been defined by NTA benchmarks to both the service provider and the auditor. The checklist should not be considered verbatim for the purpose of audit compliance. The overall intent of the government body is to protect the user of service and provider of service from any malicious attacks and threats and build confidences in the technology and service.
Keeping the overall intent in mind, we should take this opportunity to assess the overall maturity of our cyber security framework and addressing any vulnerabilities and threats we find in the process. As we all would agree, change is the only constant thing in life, and so is the lurking threat of hackers with malicious intents.
READ ALSO:
The bylaws have been defined by NTA benchmarks to both the service provider and the auditor. The checklist should not be considered verbatim for the purpose of audit compliance. The overall intent of the government body is to protect the user of service and provider of service from any malicious attacks and threats and build confidences in the technology and service.
Keeping the overall intent in mind, we should take this opportunity to assess the overall maturity of our cyber security framework and addressing any vulnerabilities and threats we find in the process. As we all would agree, change is the only constant thing in life, and so is the lurking threat of hackers with malicious intents.
READ ALSO:
Published Date: May 1, 2022, 12:00 am
Post Comment
E-Magazine
RELATED Ringside View




